LostTrust Ransomware
Trust nothing
Overview
The LostTrust ransomware family has a fairly small victim pool and has compromised victims earlier this year. The encryptor has similar characteristcs to the MetaEncryptor ransomware family including code flow and strings which indicates that the encryptor is a variant from the original MetaEncryptor source.
The leaksite contains a resume of sorts, with information about their "15 years of experience". This is also reflected in the ransomware note, in an attempt to prove that they are a professional ransomware group.
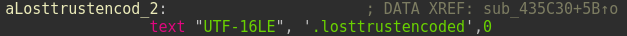
MetaEncryptor strings
Source: BleepingComputer.com
Key Take Aways
- Extensive use of command line execution to stop services
- Statically linked cryptographic routines
- Optional enumeration of network shares
Build information
Hash
- Sha256: 25a906877af7aed44c21b4c947a34666c3480629a929a227b67b273245ee3708
PDB path
The sample is built with a PDB file called fake_exe.pdb and is located in the root of the C drive. The PDB path can be found at 0x477F0 for date 8 Jul 2023 06:57
C:\fake_exe.pdb" @ file+0x477F0
Suspicious imports
A number of imports are typical, however two stand out as suspicious and are commonly found in other types of malware, especially ransomware.
- psapi.dll : The GetModuleFileNameEx() function, which can lead to identifying where a process was launched based on a fully qualified path.
- mpr.dll : The WNetEnumResource() , WNetOpenEnum() , WNetCloseEnum() calls are typically associated with identifying network shares.
Compiler
The sample was compiled as a 32-bit application using Microsoft Visual C++ 2017
Entropy
The overall average entropy of each section is 6.7, which does not indicate any type of packing involved. This was confirmed while disassembling and analyze the sample.
Preparing the system
Disable error reporting
The sample starts off by changing the error mode to not display the Windows error reporting dialog, and not the display the critical error handler message box using the kernel32.lib SetErrorMode() function. This allows increases the chances of not notifying the user of a potential issue if a critical error occurs while stopping services or processing of files.
Status updates
The next step is to check if a console is attached to the current process, if not create a new one and attach it to the current process ID using AllocConsole() , GetCurrentProcessId() and AttachConsole() . The sample has a number of logs lines to audit the status of the process, it needs to ensure it has at least one console object attached to convey the status updates.
Obtain cryptographic handle
The Microsoft cryptographic provider instance is acquired via the CryptAcquireContextW(), this will allow the sample to further make use of the cryptographically secure psuedo random number generator. The handle is used throughout the rest of the sample.
System information discovery
The sample gathers a number of states of the system using common Windows functions and storing them for reference.
Inhibit system recovery
Around 70 commands are setup to stop various services before the file discovery and encryption handler starts to process files. The sample attempts to ensure that the processes which may have sensitive files locked are killed. No stealth is used as the sample performs a series of calls to the ShellExecuteExA() function to execute each command in a row. The command window will be hidden while executing each one of the commands.
The sample will close each process by first getting a snapshot of all the running processes using the CreateToolhelp32Snapshot() function to obtain the current list of processes. For each process in the snapshot, the sample will iterate through and get the process information via the GetProcessModuleInfo() call, then if process matches the executables name, it will close the process via the CloseProcess() call.
///////////////////
// Process List
///////////////////
"rundll32.exe"
"werfault.exe"
"explorer.exe"
"vmnetdhcp.exe"
"vmware-authd.exe"
"vmware-hostd.exe"
"vmware-tray.exe"
"vmware-usbarbitrator64.exe"
"vmware-usbarbitrator32.exe"
"webroot_updater.exe"
"windowsupdate.exe"
"vmware-usbarbitrator.exe"Encryptor
File discovery & Network shares
The pipeline processing starts off by creating a new thread to update the console title routinly. This acts as the ransomwares status indicator.
The services and processes above are handled through the creation of another thread, dedicated to preparing the system prior to file discovery.
The sample accepts two different arguments which control the flow of the sample.
--onlypath: used to process a specific directory
--enable-shares: used to process file shares using the WNetEum*() functions mentioned above.
Once the sample finishes preparing the system and options used to control the flow of the encryption handler, the next step is to discover the filesystems via the GetLogicalDriveStringsW() and GetDriveTypeW() functions.
While processing regular files and directories, the sample will attempt to identify their attributes to ensure they are infact files that can be encrypted. Once identified the ransomware will begin filtering for specific file paths and extensions, this ensures the sample includes the most important files and ignores files that may impact the stability of the system.
//////////////////////////
// Important Paths
//////////////////////////
"%windir%"
":\\$RECYCLE.BIN\\"
"\\windows\\system32\\"
"\\windows\\syswow64\\"
"\\windows\\system\\"
"\\windows\\winsxs\\"
"\\System\\msadc\\"
"\\Common Files\\"
"\\WindowsPowerShell\\"
"\\Program Files\\Internet Explorer\\"
"\\Program Files\\Microsoft Games\\"
"\\all users\\microsoft\\"
"\\inetpub\\logs\\"
":\\boot\\"
":\\system volume information\\"
":\\drivers\\"
":\\wsus\\"
"\\cache\\"
"\\cache2\\"
"\\far manager\\"
"\\ida 7.0\\"
"\\ida 6.8\\"
"\\Temporary Internet Files\\"
"\\Temp\\"
"$windows.~bt"
"$windows.~ws"
"\\google\\"
"\\mozilla\\"
"\\tor browser\\"
"\\windows.old\\"
"\\intel\\"
"\\msocache\\"
"\\perflogs\\"
"\\ProgramData\\Microsoft\\"
"\\Application Data\\Microsoft\\"
"\\All Users\\Microsoft\\"
"\\Roaming\\Microsoft\\"
"\\Local\\Microsoft\\"
"\\Local Settings\\Microsoft\\"
"\\LocalLow\\Microsoft\\"
"\\Common\\Microsoft\\"
"\\Sophos\\"
"\\Symantec\\"
"\\Leaked\\"//////////////////////////
// Exclude files
//////////////////////////
"autorun.inf"
"boot.ini"
"bootfont.bin"
"bootsect.bak"
"desktop.ini"
"iconcache.db"
"ntldr"
"ntuser.dat"
"ntuser.dat.log"
"ntuser.ini"
"thumbs.db"
"bootmgr"
"!losttrustencoded.txt"
"! cynet ransom protection(don't delete)"//////////////////////////
// File Extensions
//////////////////////////A list of the extensions can be found here: Github source
Enumerating Shares
If the option for --enable-shares was used, the sample will attempt to discover shares and process their locations using the WNetOpenEnumW(), WNetEnumResourceW() functions. The locations will be processed when performing file discovery.
Encryptor handler
The cryptographic functions are statically linked to the program and contain implementations for RC4, AES and DES. The sample will chose AES to encrypt the file contents using public key.
Once the file discovery has files to process, the encryptor logic will then encrypt the file and drop the read me note.
Once completed, the files new extensions will be '.losttrustencoded'
YARA rule
/*
MIT License
Copyright 2023 ShadowStackRe.com
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the “Software”), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
*/
rule LostTrust {
meta:
description = "rule to detect LostTrust ransomware"
author = "ShadowStackRe.com"
date = "2023-11-26"
Rule_Version = "v1"
malware_type = "ransomware"
malware_family = "LostTrust"
License = "MIT License, https://opensource.org/license/mit/"
strings:
$strOption1 = "--onlypath" ascii wide
$strOption2 = "--enable-shares" ascii wide
$strEncodedLog = "ENCODED : %ws (total files : %d)" ascii
$strExt = ".losttrustencoded" ascii wide
$strDecryptLog = "decrypt file %ws, %ws" ascii
$strReadMe1 = "So we decided to change our business model." ascii
$strReadMe2 = "This is serious business for us" ascii
condition:
all of them
}